-
Robot
Most Wanted

- Rep Power
- 82
 SK Hynix DDR5 DIMMs Vulnerable to "Phoenix" Rowhammer Attack, ECC DIMM
SK Hynix DDR5 DIMMs Vulnerable to "Phoenix" Rowhammer Attack, ECC DIMM
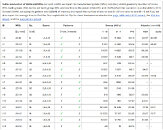
Researchers from ETH Zurich and Google have shown that SK Hynix DDR5 modules remain vulnerable to a new Rowhammer variant they call Phoenix (CVE-2025-6202), even with on-die ECC memory modules. The attack can be executed in only 109 seconds, making it a very realistic threat. By reverse engineering the built-in DRAM mitigation (TRR) for the already existing Rowhammer exploit, the team found a blind spot in the refresh-sampling logic: the mitigation's sampling period repeats every 128 tREFI intervals and, within those intervals, the first two of four sub-intervals are "lightly sampled." Leveraging this, the researchers crafted two novel long-running hammer patterns: a shorter 128-tREFI pattern and a much longer 2608-tREFI pattern. They later coupled them with a new self-correcting refresh synchronization method that realigns the attack whenever a refresh is missed. This synchronization is what lets Phoenix maintain alignment across thousands of refresh intervals, something prior routines like Zenhammer could not do reliably.
On 15 SK Hynix DDR5 modules, manufactured between late 2021 and late 2024, every module flipped bits under one of the two patterns. The 128-tREFI pattern was about 2.62× more effective on average. The team observed thousands of bit flips per DIMM and turned those flips into real-world primitives: page-table corruption, yielding arbitrary read/write access, extraction of valuable RSA-2048 keys from co-located VMs in many cases, and local privilege escalation by corrupting the sudo binary on some DIMMs. To increase the probability of hitting a vulnerable refresh offset (only 2 of 128 offsets are vulnerable, which is 1.56%), they run four shifted pattern instances across each of the four banks in parallel, boosting the hit probability by 16× to roughly 25%.
Read full story
More...
 Posting Permissions
Posting Permissions
- You may not post new threads
- You may not post replies
- You may not post attachments
- You may not edit your posts
-
Forum Rules










